Use Cases
- On-premises servers behind corporate firewalls
- Cloud VPCs (AWS, Azure, GCP) without public endpoints
- Kubernetes clusters with internal-only services
- Development environments and localhost
- Any system that only allows outbound connections
- Internal REST APIs
- Databases (MySQL, PostgreSQL) in private subnets
- Windows file shares (SMB) on corporate networks
- SFTP servers behind firewalls
How It Works
The gateway agent runs in your private environment and establishes an outbound WebSocket connection to superglue Cloud. When a tool needs to access a private system, superglue routes the request through the gateway.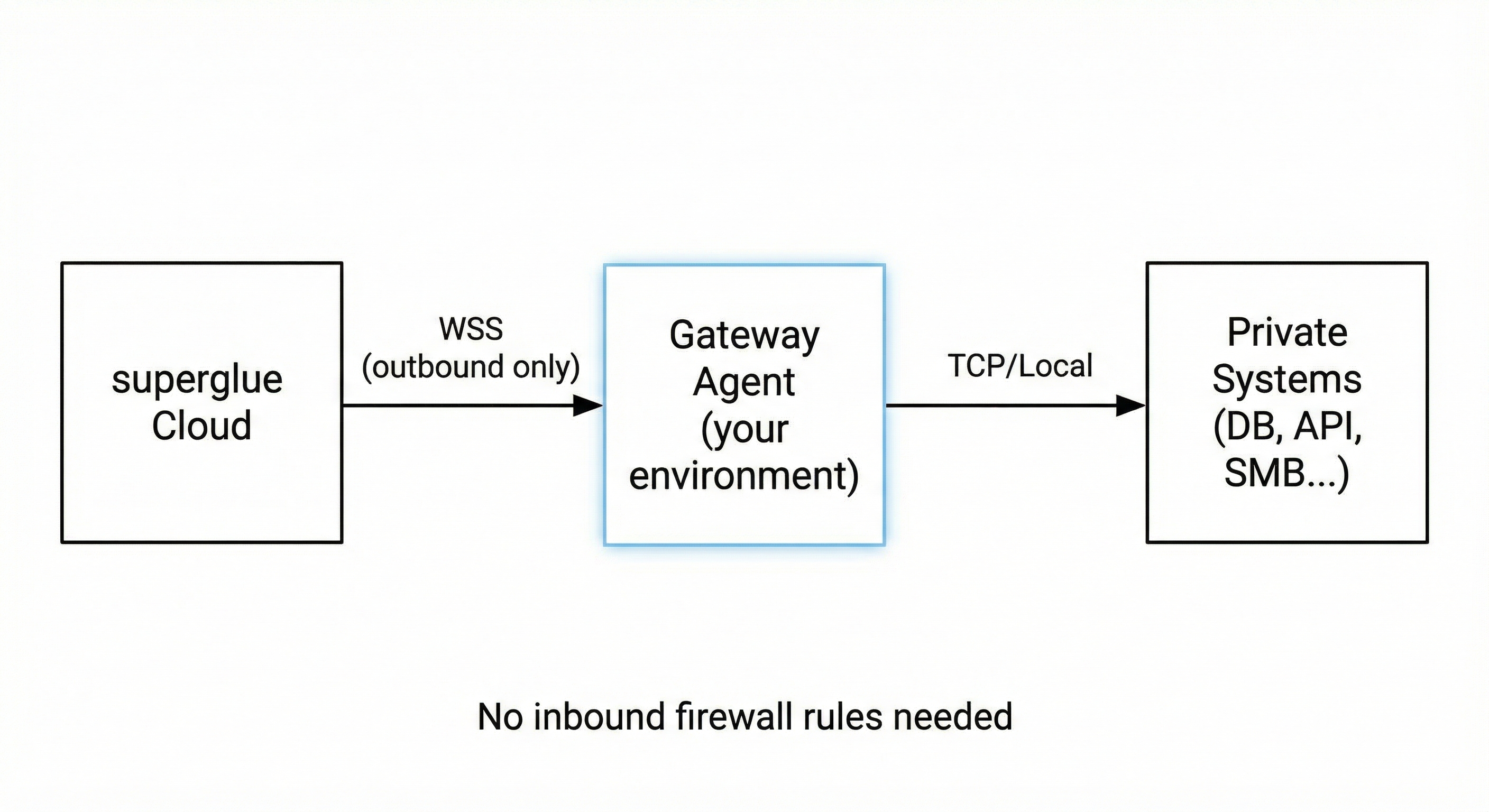
- No inbound firewall rules required
- All traffic encrypted via TLS
- Agent only exposes explicitly configured targets
- Credentials stay in your environment
Installation
Download Pre-built Binary
Configuration
Create aconfig.yaml file with your settings:
- REST API
- AWS VPC
- PostgreSQL
- MySQL
- SFTP
- Multiple Targets
Configuration Options
| Field | Description | Required |
|---|---|---|
tunnel_id | Unique identifier for this gateway connection. Appears in superglue dashboard. | Yes |
server_url | superglue WebSocket endpoint. Use wss://api.superglue.cloud/ws/tunnels for hosted. | Yes |
api_key | API key from your superglue dashboard | Yes |
targets | Map of target names to addresses. Each target becomes selectable in the UI. | Yes |
Getting an API Key
- Log in to your superglue dashboard
- Go to Settings > API Keys
- Click Create API Key
- Copy the key and add it to your
config.yaml
Running the Agent
Manual Start
Run as a systemd Service (Linux)
- Create a service file
/etc/systemd/system/superglue-gateway.service:
- Enable and start the service:
- Check status:
Run in AWS (EC2 / ECS)
For AWS VPC access, deploy the agent on an EC2 instance or ECS task within the VPC:api.superglue.cloud.
Set up your Private System in Superglue Dashboard
Once your gateway agent is running and connected:- Go to Systems in your superglue dashboard
- Click Add System and select Private System
- Select your connected gateway from the list
- Choose the target endpoint you want to use
- Configure authentication (API keys, etc.) if needed
- Add documentation for the system
- Save the system
If no gateways appear in the list, verify that:
- The gateway agent is running and connected
- The API key is valid
- The
tunnel_idmatches what you expect
Troubleshooting
Gateway won’t connect
- Verify your API key is correct
- Check that outbound WebSocket connections (port 443) are allowed
- Ensure the
server_urlis correct for your superglue instance
Target connection fails
- Verify the target address is reachable from the gateway host
- Check firewall rules / security groups between the gateway and target
- Test connectivity:
nc -zv <target-host> <port>
Connection drops frequently
- Check network stability between gateway and superglue cloud
- Review gateway logs for specific error messages
- Ensure no proxy/firewall is terminating idle connections
Security Considerations
- The gateway only exposes explicitly configured targets
- All traffic is encrypted via TLS (WebSocket Secure)
- The gateway initiates outbound connections only (no inbound ports needed)
- API keys should be kept secure and rotated periodically
- Consider running the gateway with minimal privileges
- In AWS, use IAM roles and security groups to restrict gateway access